For a while a wanted to have a LAN to LAN vpn between my own server and the server somewhere else. This would be usefull for backups and other stuff. I wanted to create a situation that clientA on network A could connect to clientB on network B, see the image below.
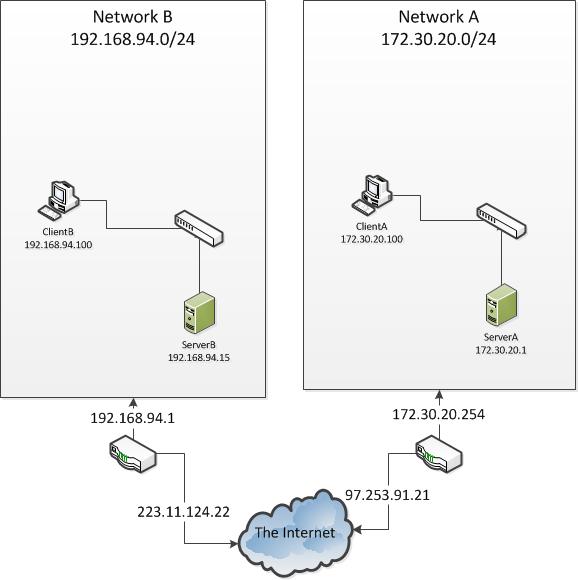
So i had some experience with setting up a OpenVPN server for clients but never LAN-to-LAN, it requires some special options to work which i will explain below. The connection will be made from ServerA to ServerB, so ServerA is the client and ServerB is the Server.
The OpenVPN config of ServerB looks like this:
client-to-client port 1194 proto tcp dev tun ca ./easy-rsa/2.0/keys/ca.crt cert ./easy-rsa/2.0/keys/server.crt key ./easy-rsa/2.0/keys/server.key dh ./easy-rsa/2.0/keys/dh1024.pem client-config-dir /etc/openvpn/ccd/ server 192.168.93.0 255.255.255.0 ifconfig-pool-persist ipp.txt push "route 192.168.94.0 255.255.255.0" route 172.30.20.0 255.255.255.0 keepalive 10 120 comp-lzo persist-key persist-tun status openvpn-status.log log-append /var/log/openvpn.log verb 3 |
Notice the client-config-dir setting. This containts a file with the same name as the client. This is necessary for routing client to client, this site explains this option. The file looks like this:
iroute 172.30.20.0 255.255.255.0 |
The config name on the client and ccd filename must be the same. On serverB in the ccd dir i have a file ServerBtoServerA and the config on ServerA is named ServerBtoServerA.conf/crt/key.
We also need to enable ip4 forwarding and nat forwarding. I have added the following lines to my firewall script which runs at server boot:
VPNRANGE="192.168.93.0/24" LANRANGE1="192.168.94.0/24" IPTABLES="/sbin/iptables" WAN_IF1="eth0" WAN_IF2="tun1" echo "checking if we need to enable IP forwarding" IPFWDCHK="`cat /proc/sys/net/ipv4/ip_forward`" if ( [ "$IPFWDCHK" != "1" ] ); then echo "IP forwarding not enabled yet enabling forwarding now" echo 1 > /proc/sys/net/ipv4/ip_forward fi echo "Setting NAT forwarding" $IPTABLES -t nat -A POSTROUTING -s $VPNRANGE -o $WAN_IF1 -j MASQUERADE |
That is all the config needed for ServerB. Below you can find the OpenVPN config for ServerA (the client):
client dev tun nobind proto tcp remote 223.11.124.22 1194 persist-key persist-tun ca ./config/ServerBtoServerA/ca.crt cert ./config/ServerBtoServerA/ServerBtoServerA.crt key ./config/ServerBtoServerA/ServerBtoServerA.key comp-lzo verb 3 |
This server only needs IP forwarding, also done in the firewall script at server boot.
echo "checking if we need to enable IP forwarding" IPFWDCHK="`cat /proc/sys/net/ipv4/ip_forward`" if ( [ "$IPFWDCHK" != "1" ] ); then echo "IP forwarding not enabled yet enabling forwarding now" echo 1 > /proc/sys/net/ipv4/ip_forward fi |
This is all the configuration that needs to be done on the servers. The only thing left to do is add routes on the client. On networkB the clients need the following routes
route add 192.168.93.0 MASK 255.255.255.0 172.30.20.1 route add 192.168.94.0 MASK 255.255.255.0 172.30.20.1 |
And the routes for networkA:
route add 192.168.93.0 MASK 255.255.255.0 192.168.94.15 route add 172.30.20.0 MASK 255.255.255.0 192.168.94.15 |
ServerA
Ubuntu server Ubuntu 9.04
OpenVPN 2.1_rc11 i486-pc-linux-gnu
ServerB:
Ubuntu server 10.04.1 LTS
OpenVPN 2.1.0 x86_64-pc-linux-gnu
References:
http://www.imped.net/oss/misc/openvpn-2.0-howto-edit.html
https://help.ubuntu.com/community/OpenVPN

This looks really neat, i bet performance is really good.
Good site, youve gotta tell us your secrets 😉 haha
After I initially commented I appear to have clicked the
-Notify me when new comments are added- checkbox and from now on whenever a comment is added I
recieve 4 emails with the same comment. There has to be a way you can remove
me from that service? Thanks!